War In Ukraine: What Is Wiper Malware That Russia May Be Using For Cyber Attacks On Ukraine - News18
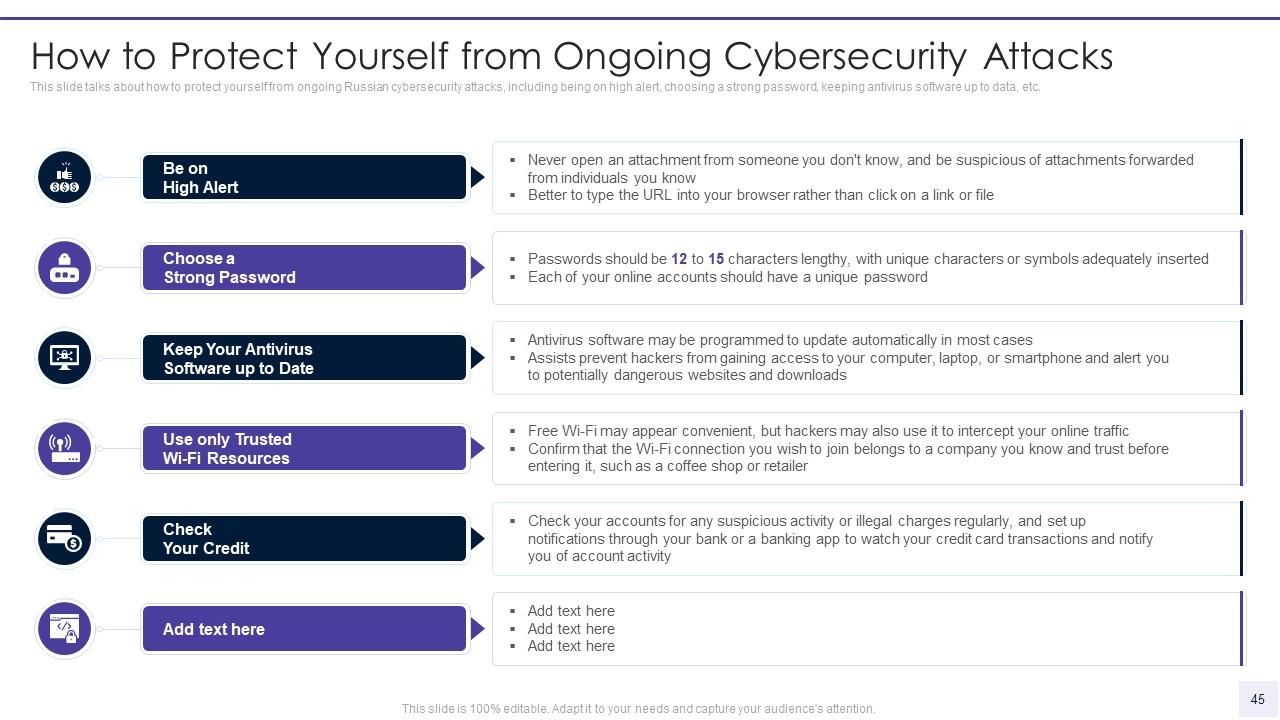
Diapositivas de presentación de PowerPoint de Wiper Malware Attack | Gráficos de presentación | Ejemplo de presentación de PowerPoint | Plantillas de diapositivas

Three Ways to Protect Your Business Against Wiper Malware: The Growing Cyber Threat - United States Cybersecurity Magazine